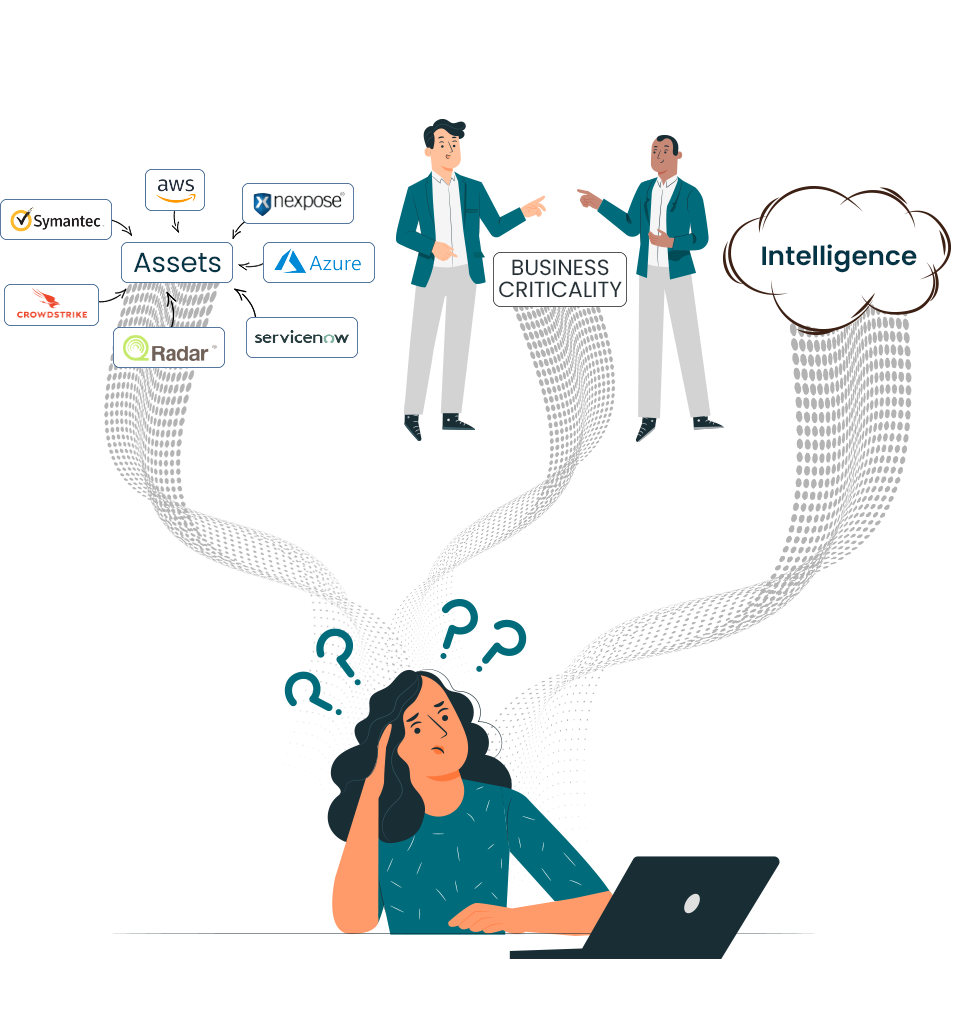
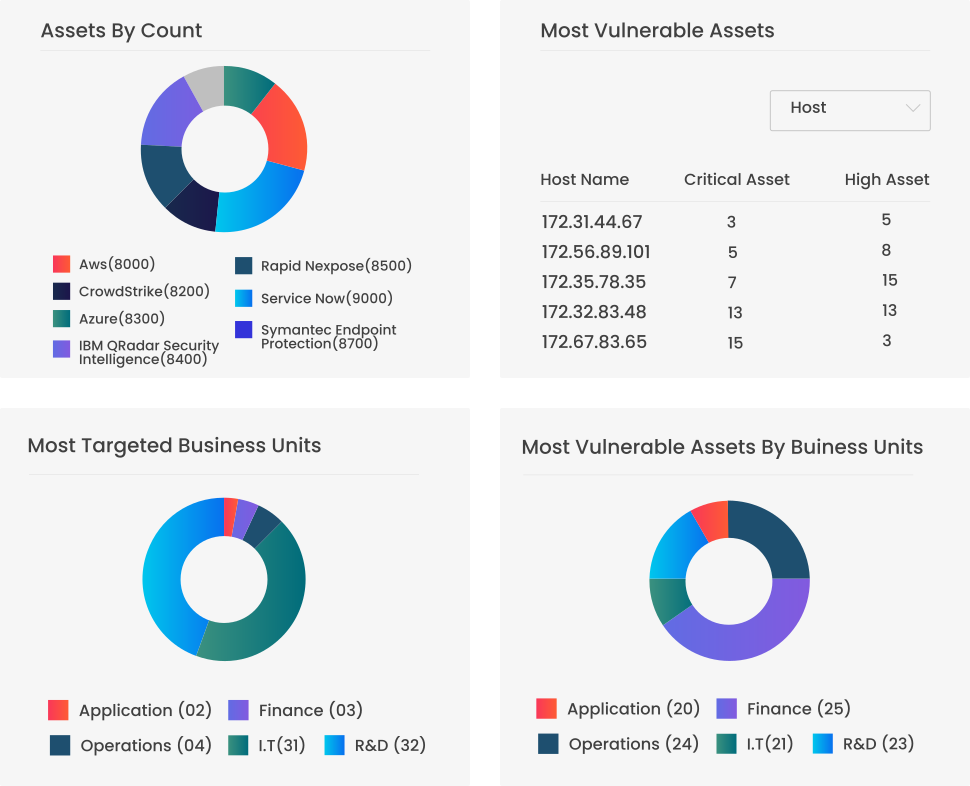
Securaa is a Comprehensive No Code Security Automation Platform that blends intelligence, risk-based asset management, vulnerability insights, automation and incident response into a single platform enabling SOC’s to reduce cybersecurity response time significantly and increase throughput manifolds.